SSH, or Secure Shell, is a widely-used protocol for secure remote access to servers and other network devices. It allows users to connect to a remote machine or server using a command-line interface and authenticate using a password or key-based authentication.
If you want to automate certain server tasks, you must run a lot of SSH code, and authentication can be handled using key-based authentication. However, if you want to use password-based authentication, it will require manual intervention.
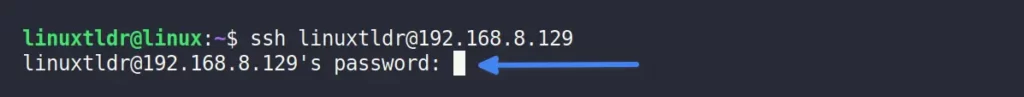
It means that you have to manually type a password for each interactive session, which is totally not cool, consumes your time, and increases the risk of a password leak.
However, this interactive method can be replaced with a non-interactive method in which you enter the password on the same line as you log in using the sshpass command-line utility.
Tutorial Details
| Description | sshpass |
| Difficulty Level | Moderate |
| Root or Sudo Privileges | No |
| OS Compatibility | Ubuntu, Manjaro, Fedora, etc. |
| Prerequisites | sshpass |
| Internet Required | Yes |
A Note for Readers
You should never use the password approach for authentication, whether interactive or non-interactive, on a server or production system.
This method always reveals your password to other users on the system. The only time I suggest you use this method of non-interactive authentication is when you’re working on something that doesn’t pose a risk even if your password leaks.
A few examples are a temporary login to a remote system, testing the automation script (when you are too lazy to create and use an authentication key), etc.
What is sshpass in Linux?
The sshpass is a command-line utility that allows automating the process of providing a password for SSH authentication, without having to manually enter the password.
This is better than traditional SSH because you don’t have to enter the password by hand. This makes the automation faster and less likely to make mistakes.
Also, sshpass gives you three ways to set the password: on the same line, as an environment variable, or in a text file. This way, you don’t have to hardcode the password into the script.
How to Install sshpass in Linux
The sshpass command-line utility can be installed in major Linux distributions by executing any one of the following commands:
$ sudo apt install sshpass #On Debian or Ubuntu
$ sudo dnf install sshpass #On Red Hat or Fedora
$ sudo pacman -S sshpass #On Arch or Manjaro
$ sudo zypper install sshpass #On openSUSE
$ brew install sshpass #Using HomeBrewOnce the installation is done, verify the presence of this command-line utility by executing the following command:
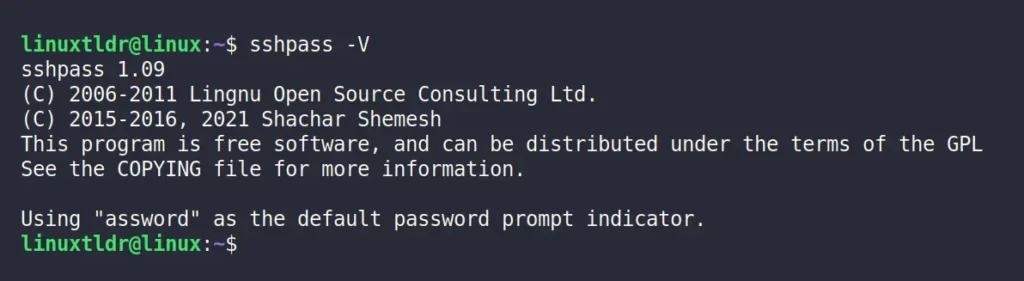
$ sshpass -VOutput:
How to Login to a Remote System Using sshpass
As I’ve mentioned earlier, this command-line utility can be used in three ways for non-interactive SSH login: by specifying the password in a same line, as an environment variable, or in a text file. Let’s start with
1. Provide Password as an Argument
In this way, use the sshpass command-line utility and provide the password as an argument to this command using the “-p” flag.
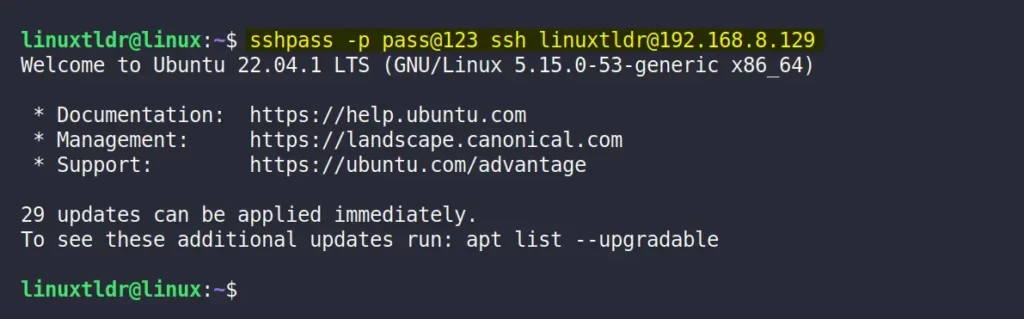
$ sshpass -p 'password' ssh username@remote_hostExample:
$ sshpass -p pass@123 ssh [email protected]Output:
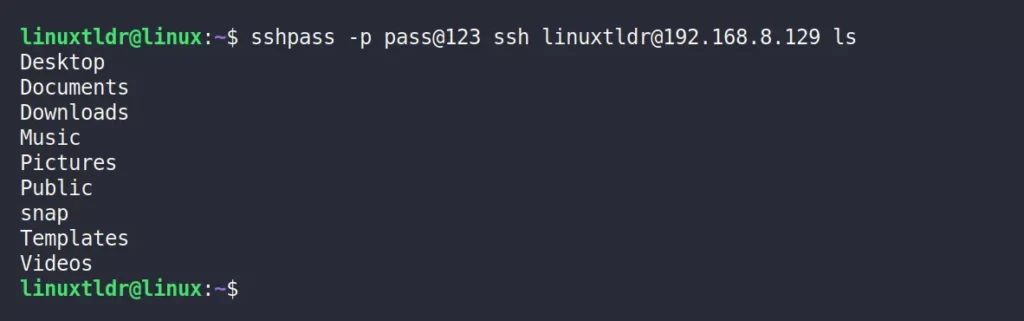
To execute a command in a non-interactive way, specify it at the end of the following command as an argument:
$ sshpass -p pass@123 ssh [email protected] lsOutput:
Now, let’s see how you can use the environment variable with sshpass.
2. Provide an Environment Variable as an Argument
In this method, you have to specify the password to the SSHPASS environment variable using the export command.
Once you’ve done that, you can use the “-e” flag to take the SSHPASS variable value as a password for the supplied SSH login.
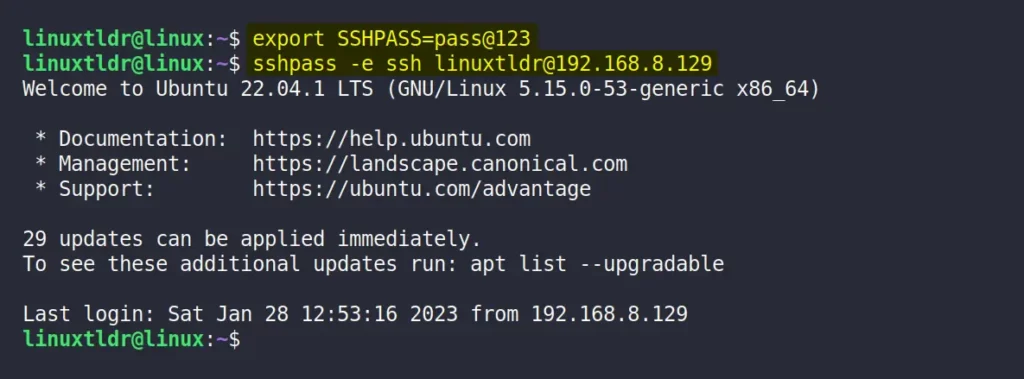
$ export SSHPASS=pass@123
$ sshpass -e ssh [email protected]Output:
3. Provide a Text File as an Argument
Unlike the previous two examples, where your password is being captured by your shell and can be shown using the history command.
You can write your password in a text file and provide the file as an input to this command to avoid your password appearing in the history record.
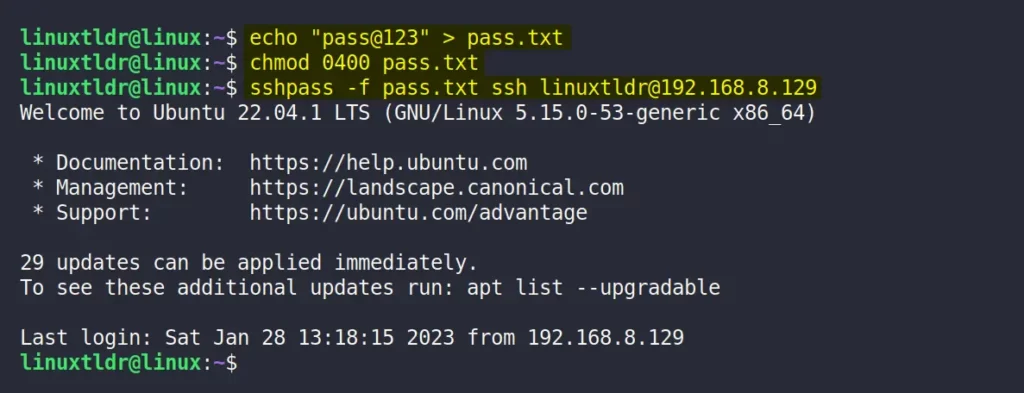
1. Append your password to a text file (ex: “pass.txt“):
$ echo "pass@123" > pass.txt2. Allow the read permission for owner and restrict for all other users:
$ chmod 0400 pass.txt3. Pass the password file as an argument to sshpass using the “-f” flag:
$ sshpass -f pass.txt ssh [email protected]Output:
4. Provide an Encrypted Password File as an Argument
The previous example, where you learn to login via text file, is better than the first and second examples. However, you can encrypt the plain password mentioned in the text file using GPG to increase the security a bit.
But this method involves multiple steps. I suggest you go with key-based authentication, but from a learning perspective, let’s see how you can use this method.
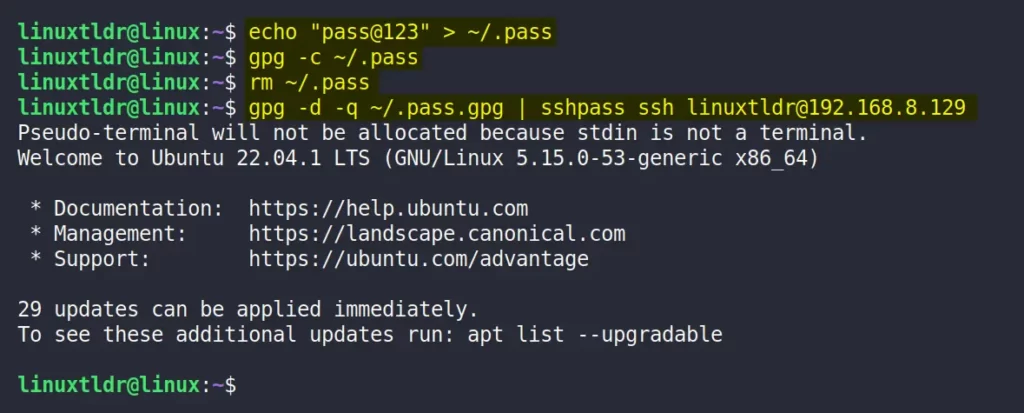
1. Append your human-readable password to a hidden text file (ex: “.pass“):
$ echo "pass@123" > ~/.pass2. Encrypt the plain password using the gpg command:
$ gpg -c ~/.pass3. Remove the plain password file:
$ rm ~/.pass4. Now use the encrypted password for non-interactive SSH login:
$ gpg -d -q ~/.pass.gpg | sshpass ssh [email protected]Output:
Usage of sshpass Command
From the previous section, you learned how you can use this command-line utility for non-interactive SSH login; now let’s see what else you can do with this tool.
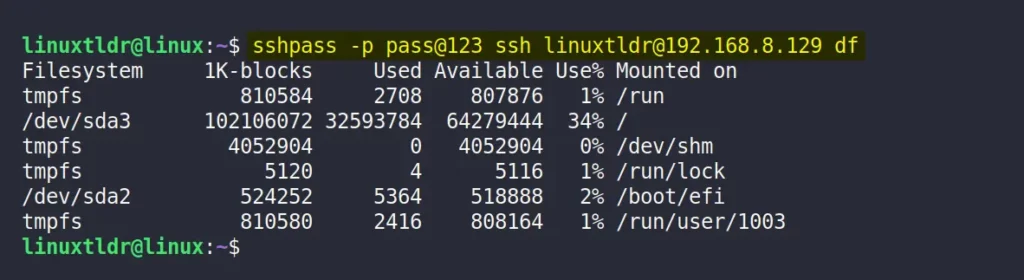
1. Execute Command Without Login
You can execute a command on a remote server in a non-interactive way (that was already mentioned in the previous section).
Just pass the command at the end of the sshpass command, as shown.
$ sshpass -p pass@123 ssh [email protected] dfOutput:
2. Execute Command with Sudo Privilege Without Login
If you are executing the command as the root user, then you don’t have to worry about anything, but most of the time it’s recommended not to use the root account while accessing remote systems via SSH.
So, I consider that you want to execute a certain command as a normal user with sudo privileges. In this case, you can either remove the sudo authentication for that command or use the “-S” flag with sudo to enter the password interactively.
$ sshpass -p pass@123 ssh [email protected] sudo -S dfOutput:
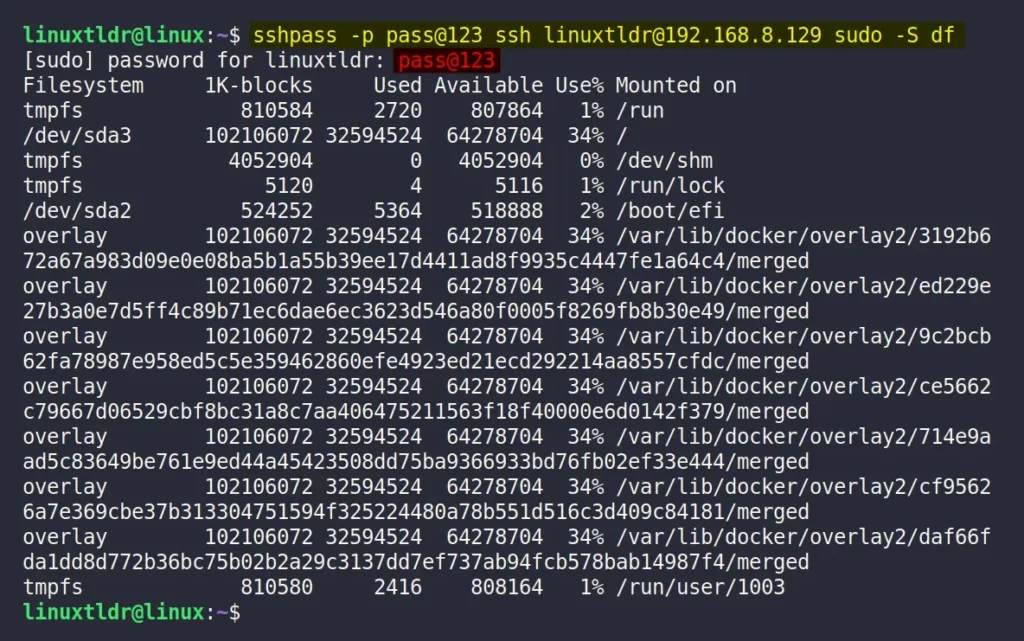
As you can see from the above picture, using this method will print the password on the screen, increasing the risk for password leaks by a malicious third party.
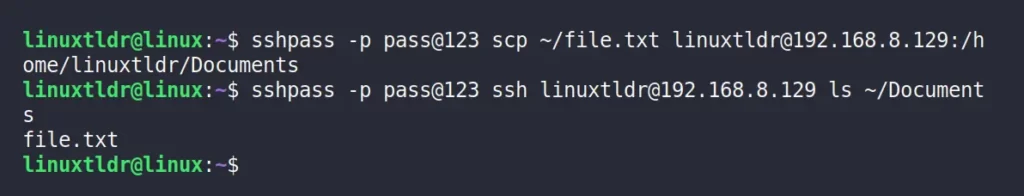
3. Copying Files From a Local Machine to a Remote Server Using SCP
You can easily copy the file from your local machine to a remote server using this tool along with scp, as shown.
$ sshpass -p pass@123 scp ~/file.txt [email protected]:/home/linuxtldr/Documents
$ sshpass -p pass@123 ssh [email protected] ls ~/DocumentsOutput:
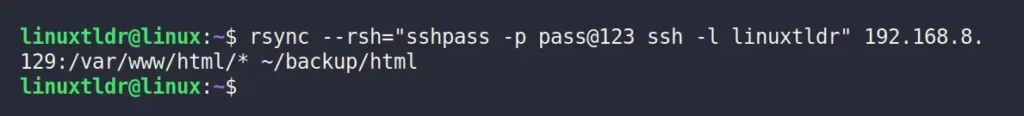
4. Transfer File Using Rsync with sshpass
You can use rsync to sync a single (log) file or the entire directory (ex: “/var/www/html“) between the local machine and the remote server, as shown.
$ rsync --rsh="sshpass -p pass@123 ssh -l linuxtldr" 192.168.8.129:/var/www/html/* ~/backup/htmlOutput:
How to Remove/Uninstall sshpass
Execute any one of the following commands to remove it from your system once you realize that it poses a major security threat to your password.
$ sudo apt remove sshpass #On Debian or Ubuntu
$ sudo dnf remove sshpass #On Red Hat or Fedora
$ sudo pacman -R sshpass #On Arch or Manjaro
$ sudo zypper remove sshpass #On openSUSE
$ brew remove sshpass #Using HomeBrewWrap Up
As you can see, the job that you expect to do with this command is absolutely done well. Only I don’t suggest you use it everywhere; key-based authentication is easier and safer than this.
If you have any questions or queries related to this article, then feel free to ask them in the comment section.
Till then, peace!